Exposures of Automotive Bus Systems
Exposures of Automotive Bus Systems - Ever since electronic devices are installed into cars, they were also always a feasible target for malicious attacks or manipulations. Mileage counter manipulation [Mos04], unauthorized chip tuning or tachometer spoofing [An98] are already common, whether still more harmless practiced examples.
Further possible electronic automotive applications like digital tachograph, electronic toll and electronic license plate or paid information services (Location Based Services) increase the incentive for manipulating automobile electronics.
Above all, unauthorized vehicle modifications can compromise particularly the driving safety of the respective car and of all surrounding road users.
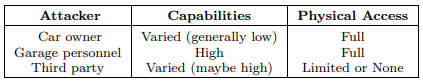
Besides the most obvious attacker, the car owner, also accordingly instructed garage employees and third parties such as competing manufactures or other unauthorized persons and institutions may have reasonable attacking intents.
Moreover, in contrast to most common computer networks, the car owner and the garage personnel have full physical access to all transmission media and respective affected devices of the automotive network.
As the car owner normally has only low theoretical and technical capabilities, garage personnel and some external third parties may have both, adequate background knowledge and the appropriate technical equipment, for feasible intrusions.
This allows deep and above all permanent manipulation in the automobile electronics. Possible motivations of third parties for breaking into automotive networks may be attacks on the passenger’s privacy (phone tapping, data theft) or well directed attacks on particular vehicle components in the case of a theft or even a potential assault.
Table 4 briefly represents the three groups of potential attackers and their respective capabilities. Apparently, technical sophisticated garage employees, acting on the owners instructions, are the most dangerous attacker group.
While current analyses [Pl02, Po01] can verify the safety and reliability of vehicle networks against random failures, most existing automotive communication systems are virtually unsecured against malicious encroachments.
Several reasons make it difficult to implement security in the vehicular area. So far, safety was the most crucial factor and therefore security was only an afterthought. Automotive resource constraints, the multitude of involved parties and insufficient cryptographic knowledge cause additional difficulties when implementing appropriate precautions.
Moreover, security may need additional hardware and infrastructures, may cause considerable processing delays and particularly generates extra costs, without apparent benefits.
Nonetheless, vehicle electrification and in-car networking proceeds unimpaired and the lack of security becomes more and more a serious risk, so the emerging challenge in automotive communication is to provide security, safety and performance in a cost effective manner.
Many typical characteristics of current automotive bus systems enable unauthorized access relatively easy. All communication between controllers is done completely unencrypted in plain text.
Possible bus messages, their respective structures and communication procedures are specified in freely available documents for the most vehicle buses. Furthermore, controllers are not able to verify if an incoming message comes from an authorized sender at all.
Nevertheless, the major hazard originates from the interconnection of all the car bus systems with each other. The net-spanning data exchange via various gateway devices, allows potentially access to any vehicular bus out of every other existing bus system.
In principle, each LIN, CAN or MOST controller is able to send messages to any other existing car controller. Hence, without particular preventive measures, a single comprised bus system endangers the whole vehicle communication network.
In combination with the increasing integration of miscellaneous wireless interfaces, future attacks on automotive communication systems can be accomplished contactless, just by passing a car or via cellular phone from almost anywhere in the world.
Breaking away the electronic mirror and connecting to the underlying LIN network with a mobile computer, could be a possible promising way to break into an expensive car today already.
Next generation future image-processing assistances for autonomous driving systems such as lane tracking or far field radars access high safety-relevant vehicular driving systems based on information from external data bases received via known quite insecure wireless links.
Besides this, interconnections of multimedia buses like MOST, D2B with the control network of the vehicle, enables software programs such as viruses or worms, received over inserted CD/DVDs, email messages or possibly attached computers, to penetrate also highly safety-relevant vehicular systems.
Even if today modern gateways already include simple firewall mechanism, most of them offer unprotected powerful diagnostic functions and interfaces that allow access to the whole car network without any restrictions.
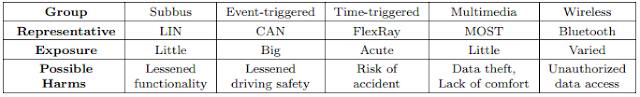
The consequences of successful attacks range from minor comfort restraints up to the risk of an accident. Therefore, the probability of an attack and the level of security required in a given bus system depends on the potential consequences of loss or manipulation.
As shown in Table 5, whereas attacks on LIN or multimedia networks may result in the failure of power windows or navigation software, successful attacks on CAN networks may result in malfunction of some important driving assistants, that leads to serious impairments of the driving safety.
A succeeded systematic malfunction on real-time buses like FlexRay, which handle elementary driving commands like steering or breaking, can lead in acute hazards for the affected passengers and other surrounding road drivers.
Nonetheless, also just a simple malicious car locking may have serious consequences for passengers [BaP03].
In the following, we describe some feasible attacks on the protocol layer of the representative car bus systems described in Section 2, assuming that we have physical or logical access to the corresponding vehicle network.
LIN
Utilizing the dependency of the LIN slaves on their corresponding LIN master, attacking this single point of failure, will be a most promising approach. Introducing well-directed malicious sleep frames deactivates completely the corresponding subnet until a wakeup frame posted by the higher-level CAN bus restores the correct state again.
The LIN synchronization mechanism can be another point of attack. Sending frames with bogus synchronization bytes within the SYNCH field makes the local LIN network inoperative or causes at least serious malfunctions.
CAN
The priority driven CSMA/CD access control method of CAN network enables attacks that jam the communication channel.
Constantly introduced topmost priority nonsense messages will be forwarded always first (even though they will immediately discarded by the receiving controllers) and prevent permanently the transmission of all other CAN messages.
Moreover, utilizing the CAN mechanisms for automatic fault localization, malicious CAN frames allow the disconnection of every single controller by posting several well-directed error flags.
FlexRay
Similar to the CAN automatic fault localization, FlexRay’s so-called bus guardian can be utilized for the well-directed deactivation of any controllers by appropriate faked error messages.
Attacks on the common time base, which would make the FlexRay network completely inoperative, are also feasible, if within one static communication cycle more than f 1 malicious SYNC messages are posted into a FlexRay bus.
Moreover, introducing well-directed bogus sleep frames deactivates corresponding power-saving capable FlexRay controllers.
MOST
Since in a MOST network one MOST device handles the role of the timing master, which continuously sends timing frames that allow the timing slaves to synchronize, malicious timing frames are suitable for disturbing or interrupting the MOST synchronization mechanism.
Moreover, continuous bogus channel requests, which reduce the remaining bandwidth to a minimum, are a feasible jamming attack on MOST buses.
Manipulated false bandwidth statements for the synchronous and asynchronous area within the boundary descriptor of a MOST frame can also make the network completely inoperative.
Due to the utilized CSMA/CD access control method used within the asynchronous and the control channel, both are vulnerable to jamming attacks similar to CAN.
Bluetooth
Wireless interconnections imply a distinct security disadvantage over wired communications in that all information is broadcasted over an open, easily tapping-capable air link. Although, Bluetooth transmissions are at least simple encrypted, there exist various feasible attacks [Ast03, BSI03, JS01]. Actually, even first worms and viruses begin infecting Bluetooth devices wirelessly [Cab04, Spg04].



Posting Komentar untuk "Exposures of Automotive Bus Systems"